Connect with us!
Discover the broad range of services we provide
Infected equipment, unauthorized personnel, and unauthorized access are affecting the security status of any industry
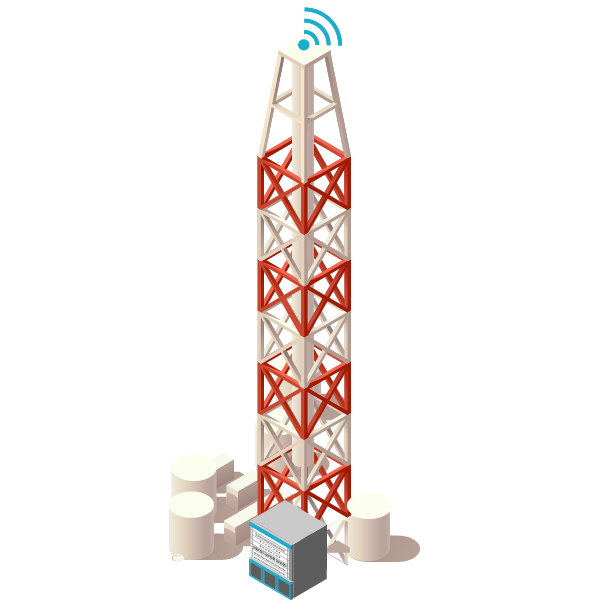
Base Transceiver Stations (BTS) are key infrastructures on any telecommunication network as they make the interface with the mobile terminals and represent 70-80% of its total energy consumption. The ability to monitor the performance of wireless communications systems, even detecting cable faults from a remote location, is becoming increasingly valuable as hundreds of new base stations come on line.
Remote monitoring equipment provides a convenient means of remotely monitoring and controlling generator sets, transfer switches, sensors and output controls. Users can monitor power generator data set including annunciator, alternator and engine data, as well as transfer switch data, such as source, load and switch connection status.
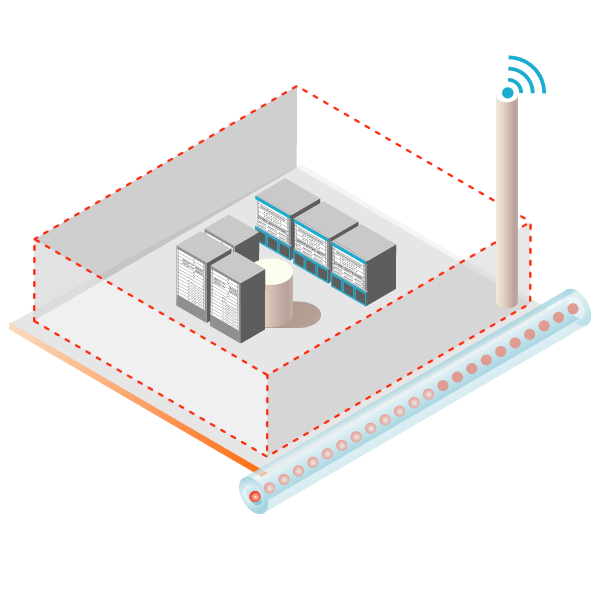
If there are weak links, then you have unprotected perimeters, which means unprotected assets, unprotected people and, inevitably, security breaches. The ramifications of these breaches can be disastrous, so the threat of intrusion remains a prime concern at all facilities. Our field-proven sensor technologies provide reliable perimeter detection options for security sensitive applications and harsh exterior environments.
Minimizing the risk and impact of advanced and targeted threats
Since the dawn of civilization, maintaining perimeter security has been a top priority. Having some form of it—whether a city wall, a moat or even trained animals—has always been critical for stopping, delaying or deterring a perimeter breach. Even with primitive perimeter security systems, having real-time intelligence and immediate response is vital.
It is imperative to take necessary precautions to ward off unwanted intruders especially if your company is involved in matters requiring high level of security.
With the trend of selling towers to independent tower companies, the operational challenges that were the Mobile Network Operator's problem are now the tower companies’ opportunities. Those opportunities include: improving site level profitability through investment in energy efficiency; reducing fuel theft; and unlocking economies of scale in maintenance processes.
With a core ability in system integration, our services allow customers to manage and scale critical infrastructure security solutions into new and current systems
Warning about threats in real time minimizes the risk and impact of advanced and targeted threats.
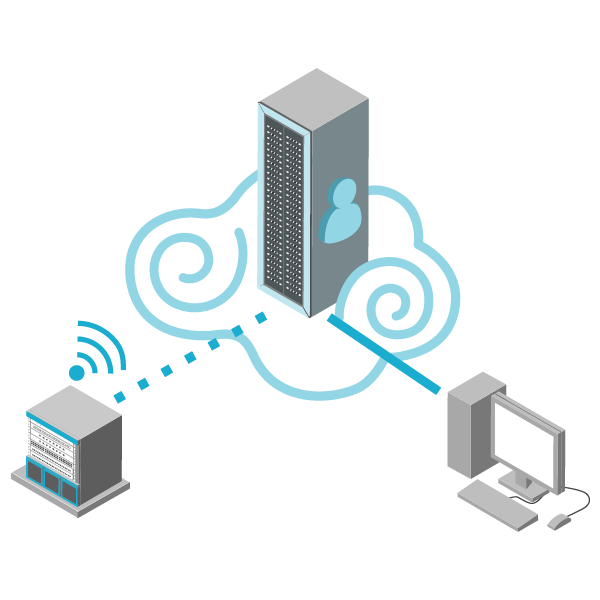
As perimeter security technology becomes more and more advanced, it is a lot easier to control and monitor these systems remotely.
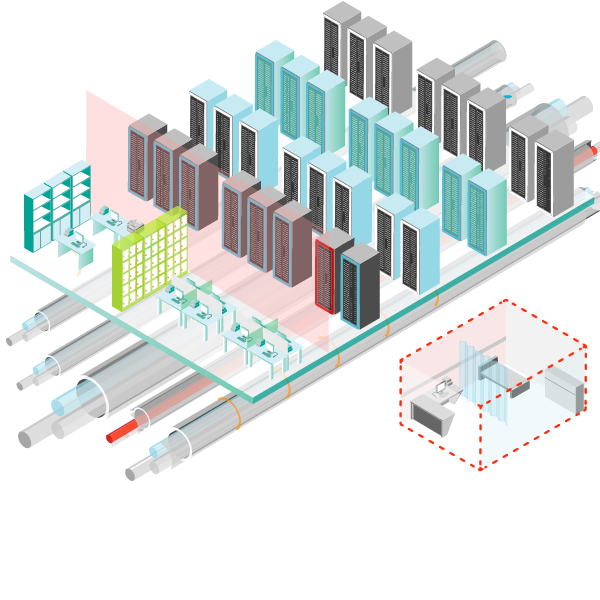
Precise disturbance location, resistance to false alarms, uniform detection sensitivity and custom controlled zoning.
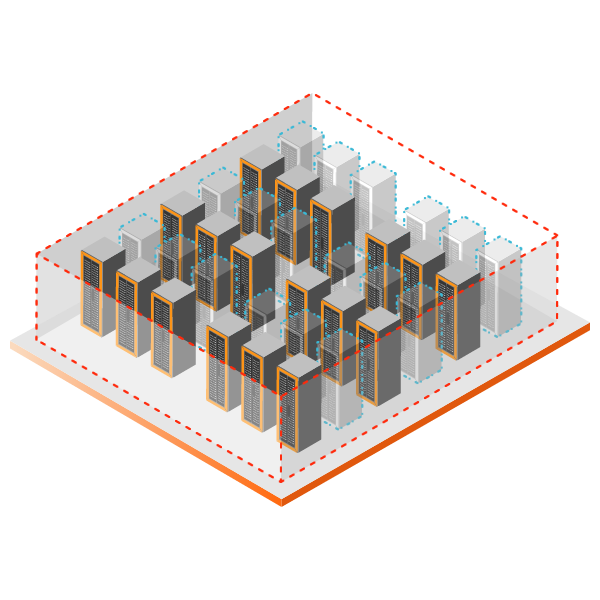
Continuous updates and comprehensive monitoring in order to adapt quickly to changing threats.
Discover the broad range of services we provide